In this post, we look at how to move data in and out of Salesforce Marketing Cloud securely. When designing data exchange processes between Salesforce Marketing Cloud and external platforms, you need to consider an appropriate file transfer protocol and file encryption.
This post discusses both of these topics and explores how to mitigate risks by applying best practice principles. Before diving into best practices, let’s take a look at marketing technology cybercrime trends and implications.
Marketing Technology Cybercrime
Cybercrime is the fastest-growing crime globally, increasing every year in size, sophistication and cost.
Cybercrime is the fastest-growing crime globally, increasing every year in size, sophistication and cost.
While cybercrime takes on many forms, unauthorized data access, or a ‘data breach’ is a common method of obtaining personally identifiable information (PII).
PII can then be further used for identity theft (which comes in different flavors), or holding organizations to ransom, where the attacker demands payment (typically Bitcoin) and threatens to publish the stolen data (typically on a website) if payment is not received.
There are several approaches to obtaining data unlawfully, but a common method is to intercept data when files are transferred across the Internet between externally-facing systems and servers.
Marketing technology stacks typically comprise of siloed cloud-based platforms that use ETL (Extract, Transform and Load) processes to exchange data between systems, including e-commerce, CRM, data warehouses, data lakes and a multitude other platforms. And Marketing Cloud is built with this requirement in mind. Automation Studio in Marketing Cloud enables automation of data processing on a triggered or scheduled basis, including the ability to import and export data using popular file transfer protocols.
While there are several file transfer options for moving data in and out of Marketing Cloud, it’s important to understand data exchange best practices to mitigate data compromise or unauthorized access by attackers.
In the next section, we take a look at secure file transfer options to move data out of Marketing Cloud and the pros and cons of each solution.
Secure File Transfer for Marketing Cloud
All Marketing Cloud editions include an SFTP account, or ‘Enhanced FTP’ where you can import data files to, or export data from. Alternatively, you can use an external FTP, FTPS or SFTP site to import and export data files from the platform. Below we cover items to keep in mind if/when leveraging FTP, FTPS, and SFTP.
FTP
FTP remains a popular file transfer method that pre-dates the Internet. Despite its maturity, FTP wasn’t developed with security in mind and on its own, is not secure.
Despite its maturity, FTP wasn’t developed with security in mind and on its own, is not secure.
With FTP, files and user credentials are transmitted without encryption, which opens them to being intercepted and read by a man-in-the-middle attack. For that reason, using FTP for data exchange with Marketing Cloud is strongly discouraged and should only be used in limited use cases or on networks that you trust.
FTPS
FTPS is an extension to FTP and adds support for the Transport Layer Security (or TLS). Similar to HTTPS, FTPS uses SSL certificates, which are signed by a trusted certificate authority, providing assurance that the client is connected to the requested server, avoiding a man-in-the-middle attack. While FTPS does provide a secure method of file transfer, it uses multiple port numbers.
While FTPS does provide a secure method of file transfer, it uses multiple port numbers.
In turn, this often requires additional firewall configuration to expose a larger number of ports to accommodate FTPS connections. This is sometimes undesirable as for security reasons; organizations prefer to limit the number of ports in their publicly facing firewalls.
SFTP
SFTP is an extension to the Secure Shell protocol (SSH) to enable secure file transfer. It does this by providing a secure connection to transfer and traverse the file system on both the local and remote host. Additionally, SFTP uses the SSH protocol to authenticate and establish a secure connection and both password or key-based authentication are supported by the protocol. SFTP is widely regarded today as the de facto protocol for secure file transfer.
SFTP is widely regarded today as the de facto protocol for secure file transfer.
Marketing Cloud offers a number of different authentication options when creating SFTP user accounts. You can choose from:
- Password
- SSH Key
- SSH Key or Password
- SSH Key and Password
While all these authentication options are secure, they ultimately rely on users to follow best practices. Key based authentication is stronger than passwords. Without diving into a technical explanation, it’s possible to guess passwords, but you can’t guess a key. However, strong passwords can effectively minimize this risk. Additionally, it’s important to apply the Principle of Least Privilege (or PoLP), where password credentials are only issued to users who require them to perform their job functions.
Also, consider adopting a password manager software to store your passwords, in preference to storing passwords in files or on paper. Furthermore, you should change passwords every 90 days or less.
Passwords best practices: only issue credentials to users who require them, use a password manager platform, and change passwords every 90 days or less.
These same rules also apply to SSH keys. Only designated users should be able to access SSH keys and it’s important to enforce diligent key rotation, while also disallowing the use of matching passphrases across multiple keys or iterations.
Deciding on the best authentication option isn’t straightforward. Both passwords and SSH keys offer their own advantages and disadvantages. However, where possible, it’s recommended that you adopt both SSH key and password authentication.
Where possible, it’s recommended that you adopt both SSH key and password authentication.
The main justification is that if your private key is compromised (for example, your device is stolen or malware is installed on it), the attacker won’t be able to compromise the SFTP account without the password. Similarly, if your password is compromised, then they will still need your SSH key. It’s still not foolproof, but this does provide dual-factor authentication and makes it harder for an attacker to compromise your credentials.
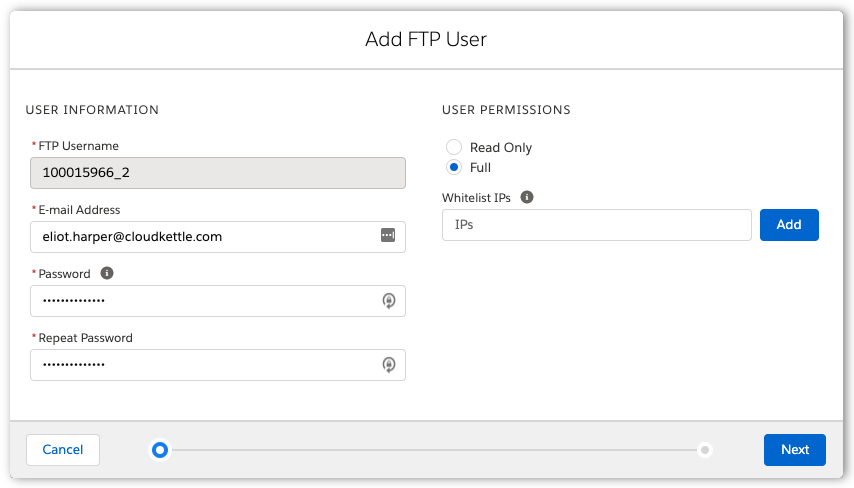
SFTP User Security in Marketing Cloud
When creating new SFTP users in Marketing Cloud, there is an option to set the user permissions to ‘Read Only’ or ‘Full’. If you are using a dedicated SFTP user account that will only retrieve files from Marketing Cloud, consider using the ‘Read Only’ option, to prevent files from being uploaded, overwritten or removed. Just because a platform or user needs permission to download files from a directory, doesn’t necessarily mean they require total rights to the directory. As an additional security layer, you should also consider enabling IP allowlisting (formerly whitelisting) for SFTP user accounts.
As an additional security layer, you should also consider enabling IP allowlisting for SFTP user accounts.
This feature allows you to define lists of trusted IP addresses or IP ranges from which the SFTP host can be accessed from.
Adding an SFTP User in Marketing Cloud
File Transfer Encryption in Marketing Cloud
When transferring files to and from Marketing Cloud by SFTP, you should also consider encrypting your files using PGP. While you may assume that SFTP replaces the need for PGP, it doesn’t. SFTP and PGP have two different goals. PGP encrypts the data payload, while SFTP encrypts the file transfer. At a minimum, you need transport encryption.
PGP encrypts the data payload, while SFTP encrypts the file transfer. At a minimum, you need transport encryption.
On top of that, data encryption is only going to help. Marketing Cloud supports importing and exporting both PGP and GPG files. GPG and PGP are almost identical, with the major difference between them being how they are licensed to the public. PGP or GPG encryption protects your data at rest, which ensures that the data file is not exposed after it’s transferred to an SFTP server or file system.
You can encrypt data files that you transfer to Marketing Cloud using their PGP public key, which is available here. To encrypt data files that are transferred from Marketing Cloud, you can upload your own public PGP or GPG key on the Key Management page in Marketing Cloud setup, choosing the ‘Asymmetric’ key type.
In this hands-on tutorial video, I demonstrate how to encrypt and decrypt PGP files in Marketing Cloud.
Your Responsibility
Cybercrime is a growing concern for many enterprises and personally identifiable information is an increasingly popular target for attackers. While marketing technology platforms, like Salesforce Marketing Cloud, provide the ability to securely exchange data, breaches can occur when platforms are not optimally configured or internal security policies are not enforced.
As these attacks continue to become more advanced, organizations need to adapt their defence layer and brace themselves for this emerging wave of sophisticated onslaught, while also taking on a greater responsibility and obligation to protect their customers’ data.
We hope you found the actionable insights provided in this post helpful. If you have questions about this blog or how to improve Marketing Cloud security, reach out today. We love helping enterprise companies succeed with Salesforce Marketing Cloud.