As a business grows and its Salesforce org matures, the number of Profiles and Permission sets can start to increase. If there is no process in place, managing profiles and permission sets in a Salesforce org can become a complex and challenging task for an admin, especially when there are a large number of them coupled with unclear naming conventions or descriptions. In this blog post, we will explore the best practices for cleaning up profiles and permission sets in a Salesforce org, as well as optimizing their management for improved efficiency and compliance.
Profiles: Minimize, Merge, and Delete
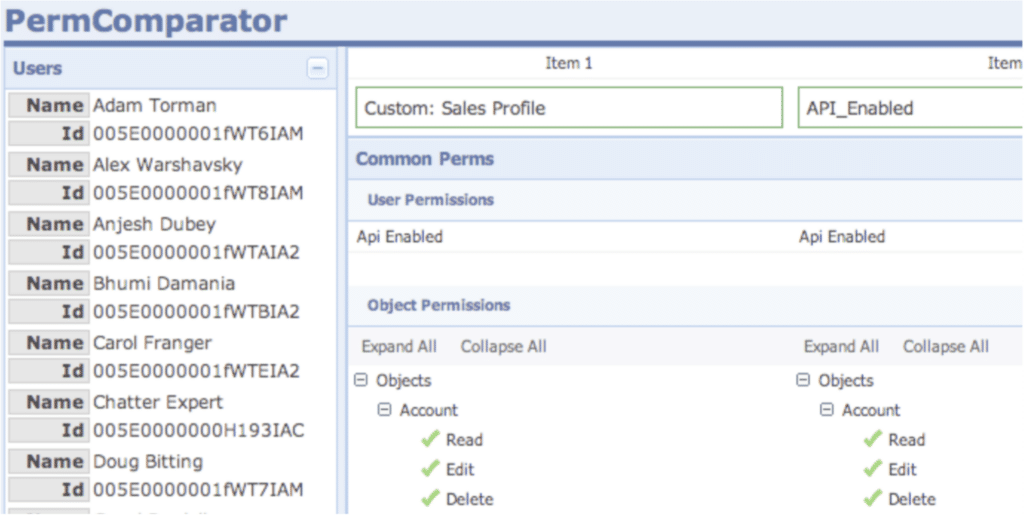
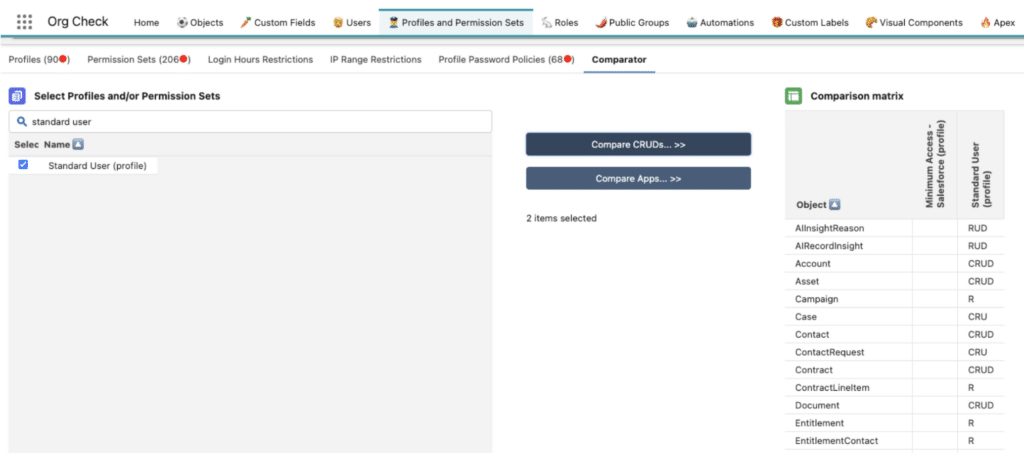
The first step in cleaning up profiles is to reduce their number to match the number of personas identified by the business. To achieve this, merge profiles with similar permissions together. This can be done using a permission comparison tool that assesses the similarities and differences between profiles. Some useful tools for this purpose include Perm Comparator and the Org Check App. Additionally, unassigned profiles that are not standard Salesforce profiles should be deleted to reduce clutter and confusion.
Figure 1. PerComparator Heroku App
Figure 2. Org Check App
Permission Sets: Delete, Document, and Compare
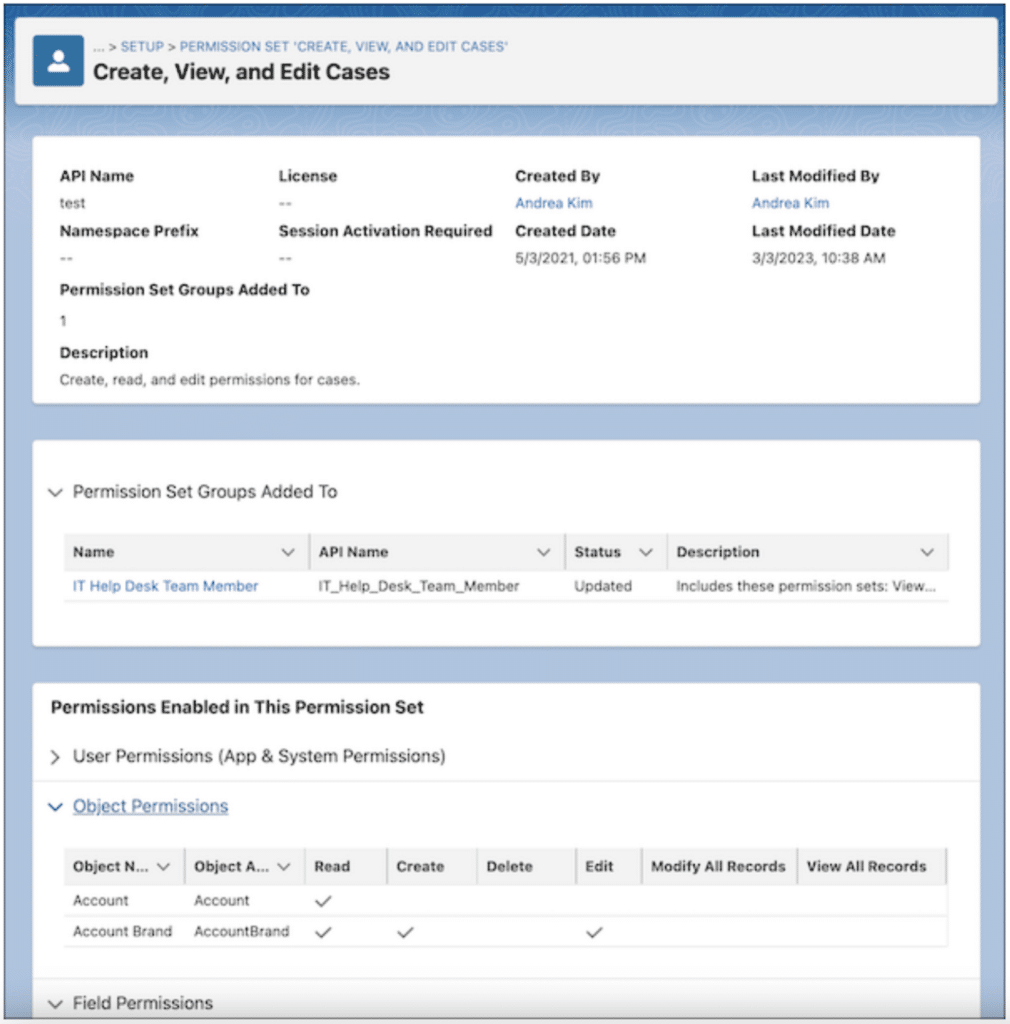
Similar to profiles, unassigned permission sets should be deleted from the org to streamline the permission management process. Tools like the Org Check App can help identify which permission sets are not assigned to any users. The upcoming “View Summary” native Salesforce feature currently in beta will be a helpful tool as well for admins to determine the permissions a permission set grants from a single screen. It is also important to have proper documentation, including naming conventions and descriptions, for each permission set. This ensures that administrators and developers can easily understand the purpose and scope of each set and avoid creating duplicates when responding to access requests.
Figure 3: Permission Set – View Summary (Beta)
Granular Control with Permission Sets
Salesforce continues to promote the use of permission sets for managing user permissions, emphasizing their flexibility and efficiency. Granular permission sets based on Object permissions, field-level security, Apex classes, or App access enable administrators to define precise access rights for different users. For example, a granular permission set can grant Create, Read, and Update permissions on the Opportunity object.
By assigning permission sets to existing profiles, administrators can simplify user access management and reduce the need for multiple profiles to accommodate different access requirements. This helps prevent profile proliferation and makes it easier to adjust permissions for multiple users.
Granular permission sets also serve as the building blocks for custom permission-set groups which leads us to our next section.
Permission Set Groups: Enhanced Permission Management
Released in Winter 22, Permission Set Groups introduce a significant improvement in permission management. They offer a balanced solution between traditional profiles and individual permission sets. Permission Set Groups allow bundling multiple permission sets together and assigning them to users, simplifying the architecture and enhancing clarity. By establishing a well-structured and meaningful permission model, administrators can reduce reliance on profiles and streamline assignments.
With Permission Set Groups, administrators can create baseline sets for different user roles or personas. These groups can be layered on top of user profiles, ensuring that specific permissions are assigned to users based on their roles. The granular permission sets mentioned in the previous section can be used to customize permissions for specific objects and fields. For example, a “Marketing User” permission set group can be granted precise access to marketing-related objects and fields. This approach enhances security, efficiency, and streamlined management of user permissions over time. The permission set group can be assigned to groups of users based on business units, roles, or departments, simplifying access management.
One important thing to note about Permission Set Groups is that there has been a reported issue with applying permissions from managed package permission sets (e.g. CPQ or Quip) within a Permission Set Group. You can view the Salesforce Issue here. Although it is possible to add them to a group, there is a small possibility that the permissions may not be applied when you assign this group to a User. In our experience, it usually works, but the issue is intermittent.
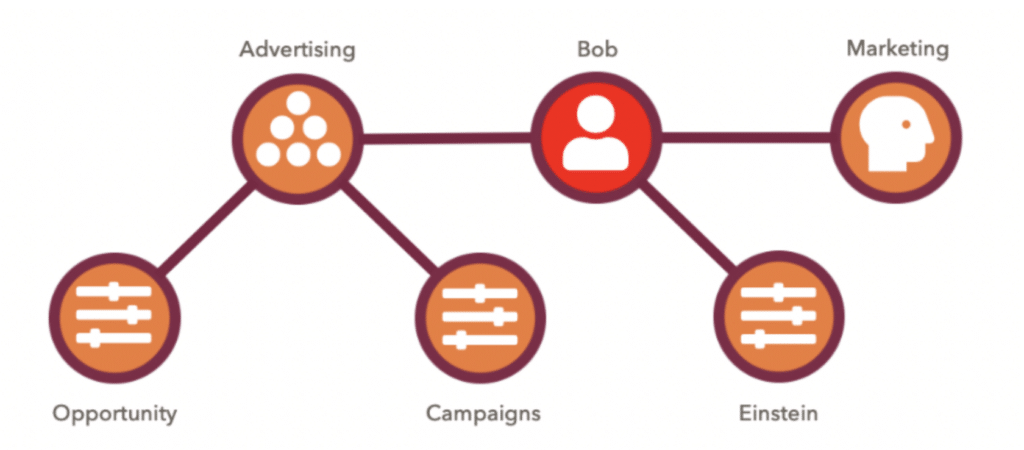
Figure 4: Permission Set Group Example (Appleton and Lefebvre)
The above example from Bill Appleton’s article on Permission Set Groups demonstrates how the Opportunity and Campaign permission sets can be grouped together in an “Advertising” permission set group. This group can then be assigned to Bob, who is a member of the Advertising Team. This approach simplifies permission management, as the admin only needs to assign the permission set group instead of issuing multiple permission sets individually.
Best Practices for Documentation and Naming Conventions
Proper documentation, clear naming conventions, and descriptions are crucial for effective profile and permission set management. A consistent naming convention throughout the organization quickly communicates the purpose and scope of each profile or permission set, making user assignment straightforward and reducing the risk of assigning incorrect permissions. Detailed descriptions also inform administrators about the included permissions at a high level, saving them from sifting through pages of permissions. These practices streamline admin onboarding, user management, and issue resolution.
For profile naming conventions, we suggest using a format such as “Company Name-User Role-License Type” or an example like “CloudKettle-Sales Team User-SF”. Additionally, we recommend creating a list view that filters by “Company Name” to improve readability among the many standard or managed package profiles in the organization.
For permission sets, we follow a naming convention like “Company Name-Permission Type-CRUDVM” or include a description of the permission. For example, a granular permission set granting create and read permissions on the Opportunity object would be named “CloudKettle-Opportunity-CR”. The following acronyms are used for permission types:
- OBJ – Object permissions (CRUDVM)
- FLS – Field Level Security
- SYS – System Permissions
- APP – Application assignment
- APEX – Apex class assignment
Documentation and naming conventions facilitate understanding and maintenance of profiles and permission sets as organizational needs evolve.
Automating Permission Assignment with Flows
Automation can significantly improve the efficiency and accuracy of permission assignments in a Salesforce org. Flows can be used to automate the process of assigning permission sets to new users. By building a record-triggered flow that assigns a predefined permission set group to each new user, administrators can reduce the guesswork and manual effort involved in assigning profiles and permission sets. The Salesforce Admin website has an article and video that goes into detail about creating this automation.
Another automation worth exploring is the assignment of permission-set groups based on user roles or a custom picklist field on the User record. This picklist field can be used to identify attributes such as a line of business or a specific office branch. By selecting the appropriate value in the picklist field, such as “Sales Team,” the corresponding permission set group can be automatically assigned to the user.
Conclusion
If not properly monitored and maintained, permission sets can quickly get out of hand in a Salesforce org. By minimizing profiles, merging similar ones, and deleting unassigned profiles you can take steps towards optimizing management, efficiency and compliance of profiles. Similarly, when dealing with permission sets, it’s important to delete unassigned permissions sets and create clear documentation and naming conventions to remove the guesswork. Finally, by embracing permission sets and automations, Admins can streamline things even further by using flows to assign permission-set groups. By implementing these practices, administrators can effectively manage profiles and permission sets, ensuring compliance and efficient user access management.
Need some assistance getting your own Profiles and Permissions under control? We would love to help! Get in touch and we’ll talk through how to optimize your org.