How to Monitor the Security of your Salesforce Instance
Monitoring Salesforce is key to ensuring the overall security of your instance doesn’t degrade over time. Often well-meaning employees make mistakes or inadvertently take actions that can create vulnerabilities in your instance. In this post, we cover five items that should be constantly monitored in Salesforce to keep your Sales Cloud data stable and protected.
1. Connected Apps
With the rise of OAuth, it’s easier than ever before for employees to install an App in Salesforce. This is problematic because not all employees understand (nor should they be expected to) all the factors that are taken into consideration when vetting if a 3rd party application should have access to Salesforce.
For this reason, it’s important to keep track of what Apps are connected with Salesforce and remove any that have not been vetted, are no longer in use, or violate your organization’s policies. The reason to track these is that applications are often granted Admin-level access to Salesforce data; which means they have access to create or delete Users, delete Records, reset User’s passwords and more. We recommend that Integrations be connected to Salesforce using a Dedicated Integration User, for more information check out this blog post, as no integration should ever be given Admin-level access to Salesforce. However, for many organization’s this is still the norm.
Enabling the App Allowlisting (formerly Whitelisting) feature in Salesforce can help manage what Users have permission in Salesforce to install which Apps. This is a feature we always recommend enabling within Salesforce to increase security. For details on how to enable App Allowlisting in Salesforce check out number four in this post: Top Five Salesforce Security Tips to Make Your Instance More Secure.
However, even if you do have App Allowlisting enabled, you’ll still want to report on what Apps are installed in Salesforce. Human error is always possible, especially if your instance has multiple admins.
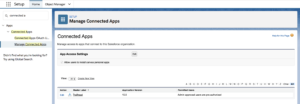
How to Report on Apps Connected to Salesforce:
Step 1: Under Setup search for Connected Apps.
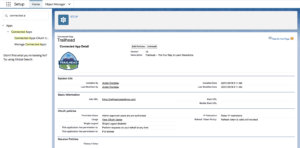
Step 2: Each App listed will show details about the App.
2. Deactivation
Another area to monitor is Users or Admins that have been deactivated because it can be a sign a User is making malicious changes. Whether it’s malicious or not, keeping tabs on how many users and who has been deactivated is smart. User freezes should also be monitored. In order to monitor this, examine the Salesforce Audit Logs and review if a User has been deactivated or frozen and by whom. This is a nearly impossible event to catch in real time and if someone is acting maliciously it will take them a short amount of time to deactivate Users. It’s good to get in a habit of checking the Audit Logs daily for these kinds of events.
3. Metadata changes
Metadata changes should also be monitored daily to ensure no malicious or flawed code has been pushed into production. Salesforce Admin(s) should be looking at all new code and examining if anything unexpected has occurred. As an example, if an employee pushes a new piece of code into Salesforce that causes data to pass into another platform, the Salesforce Admin would want to catch and reverse that change as soon as possible. This may be a violation of governance, policy, or security certification. (Example: HIPAA or SOC2)
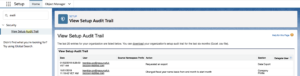
To monitor this, an Admin(s) needs to set up an Audit Trail, download the report of the last six months, sort through the CSV and export daily to see Metadata changes. Then identify if any of those Metadata changes seem irregular or may be a cause for concern. This is time-consuming, tedious work for Admins and is often overlooked until it becomes an emergency.
Step 1: Search Setup for “View Setup Audit Trail
Step 2: Click the download link to get more than the last 20 entries.
4. Mass Data Exports
Another item to watch is mass data exports, which is relatively straightforward. Anytime anyone is mass exporting data from your Salesforce instance the Admin(s) should know about it. It’s often done innocently; however, it may be an indication a sales rep is getting ready to leave the organization and trying to take leads and customer data with them.
In the absence of a monitoring tool like Salesforce SafeGuard, this is a time-consuming process that involves checking Scheduled Jobs and the Audit Trail daily.
Step 1: To catch exports through the Data Export tool, search the Audit Trail for “Requested an Export”
5. Failed Logins
Tracking failed logins is a great way to alert your organization to suspicious behavior. If, for example, a login fails repeatedly from a country where your company has no offices and then succeeds, that could indicate a threat has gained access to Salesforce. To learn more about Salesforce basic security, check out our post on the Top Five Salesforce Security Tips to Make Your Instance More Secure.
Once identified, the right course of action might be to freeze that user, change the password quickly or watch for incoming requests. The downside to reporting on this is it cannot be done in real time. If someone malicious gains access to Salesforce, that person has free reign to export data, make changes, etc. until they are caught.
Once data has left Salesforce, there’s no retrieval process. Ideally, failed logins would be tracked in real time with a built-in alert process. However, most organizations don’t have a monitoring solution in place. Therefore, reporting is the next best option.
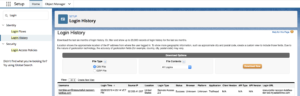
Step 1: Under Setup search for Login History. You can export this data for easier reporting.
Wrap Up
Beyond the five items we mention in this post, what needs to be monitored in Salesforce varies for each organization. Conducting a Salesforce audit, either internally or externally, will help determine what items need to be checked and at what cadence (daily, weekly, monthly, quarterly). However, once your organization reaches a certain size or has a certain number of users, investing in a real-time monitoring solution is a crucial step to keeping Salesforce secure.
Have questions about Salesforce security? Sign up for our newsletter! We send out a monthly recap of our latest Salesforce content, including articles on security best practices, actionable insight on Salesforce optimization for enterprises, and more.